Listen up, folks. If you’ve ever found yourself scratching your head wondering how to securely connect to remote servers while bypassing pesky firewalls, you’ve come to the right place. SSH through firewall isn’t just some buzzword; it’s a game-changer for IT professionals, developers, and anyone who wants to maintain secure communication in a world full of restrictions. Let’s dive right in and explore why this topic matters so much.
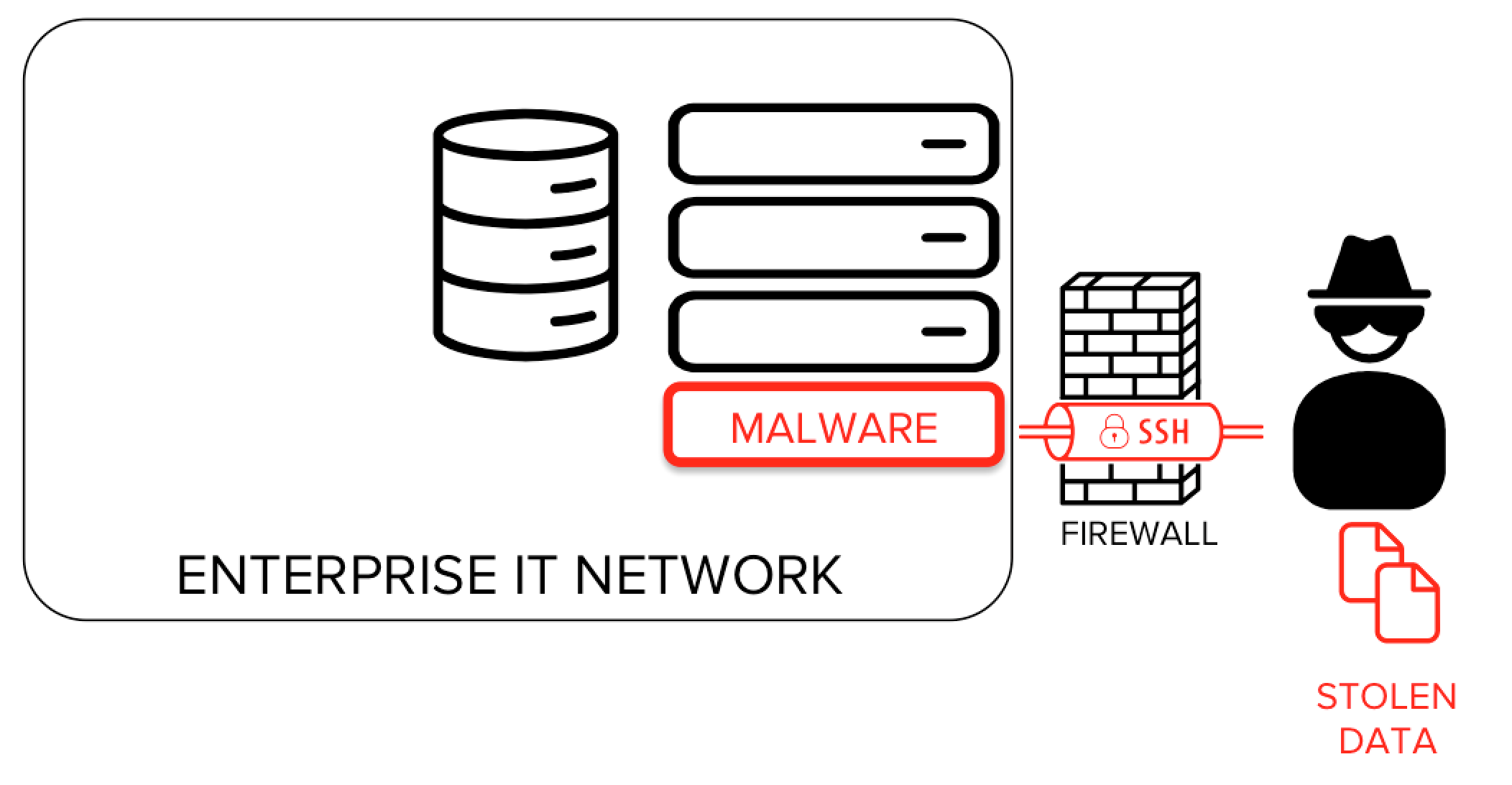
Picture this: you're sitting in your office or maybe at home, trying to access your server from behind a corporate firewall. The firewall’s like a bouncer at a club, deciding who gets in and who doesn’t. But what if you need access? That’s where SSH through firewall comes into play. It’s like having a VIP pass that lets you bypass all the restrictions and still keep your data safe.
Now, before we get into the nitty-gritty, let me tell you something important. This isn’t just about breaking rules; it’s about understanding how networks work and using tools like SSH to your advantage. So, whether you're a newbie or a seasoned pro, this guide is here to help you navigate the maze of firewalls and SSH connections. Let’s get started, shall we?
- Unveiling The Truth About Sierra Deaton A Rising Star In The Spotlight
- Fameblogs Marvins Peel Emails Address A Deep Dive Into The World Of Digital Influence
Understanding SSH: The Basics You Need to Know
Let’s start with the basics, because you can’t build a house without laying the foundation first. SSH, or Secure Shell, is essentially a protocol that lets you access remote computers securely. It’s like sending a letter in a super-secure envelope that only the intended recipient can open. But here’s the thing—firewalls sometimes block these envelopes, and that’s where things get tricky.
What Makes SSH So Special?
SSH isn’t just any protocol. It’s encrypted, meaning your data is scrambled so no one else can snoop on it. Think of it as a secret code between you and the server you’re connecting to. Here’s why SSH is so special:
- Encryption: Your data is safe from prying eyes.
- Authentication: Only authorized users can access the server.
- Flexibility: You can do a ton of things with SSH, from file transfers to tunneling.
So, when you’re trying to SSH through firewall, you’re essentially finding a way to make sure your secure connection isn’t blocked by the network’s overzealous security measures. It’s like sneaking past the guard dog, but in a totally ethical and legal way.
- Charles Shaughnessy The Man Who Left An Indelible Mark On Hollywood
- Hikaru Nagi About The Rising Star Of Anime And Voice Acting
Why Firewalls Are Both a Blessing and a Curse
Firewalls are like those strict parents who always worry about your safety. They’re there to protect your network from bad actors, but sometimes they’re a little too overprotective. When you’re trying to SSH through firewall, you’re essentially asking permission to go out and play, but the firewall’s not so sure about it.
How Firewalls Work
Firewalls monitor traffic coming in and out of a network. They use rules to decide what’s allowed and what’s not. Here’s a quick rundown:
- Packet Filtering: Examining individual packets of data.
- Stateful Inspection: Keeping track of active connections.
- Application-Level Gateways: Filtering traffic based on applications.
Now, when you’re trying to SSH through firewall, you’re dealing with a system that might block your connection because it doesn’t recognize it as safe. But don’t worry—we’ve got tricks up our sleeve to handle that.
SSH Through Firewall: The Challenges
Alright, let’s talk about the challenges. Firewalls can be pretty stubborn, and they don’t just let anyone waltz in. Here are some of the common hurdles you might face:
- Port Blocking: Firewalls often block port 22, the default SSH port.
- IP Restrictions: Some firewalls only allow connections from specific IPs.
- Deep Packet Inspection: Advanced firewalls can inspect the content of your SSH traffic.
But here’s the good news: there are ways to overcome these challenges. You just need to know the right strategies, and that’s exactly what we’re going to cover next.
Strategies for SSH Through Firewall
Now that you know the challenges, let’s talk about the solutions. There are several strategies you can use to SSH through firewall effectively:
1. Port Forwarding
Port forwarding is like giving your SSH connection a disguise. Instead of using the default port 22, you can use a different port that’s less likely to be blocked. Here’s how:
- Change the SSH port on your server.
- Update your SSH client to connect to the new port.
It’s a simple but effective way to bypass firewall restrictions.
2. SSH Tunneling
SSH tunneling is like creating a secret passage. It allows you to encapsulate other protocols within an SSH connection, making it harder for firewalls to detect. Here’s how it works:
- Create a local or dynamic tunnel.
- Route your traffic through the tunnel.
This method is especially useful for accessing blocked websites or services.
3. Using a Proxy
Sometimes, using a proxy server is the best way to SSH through firewall. A proxy acts as an intermediary, allowing you to connect to your server without the firewall knowing. Here’s what you need to do:
- Set up a proxy server.
- Configure your SSH client to use the proxy.
Proxies can be a bit more complex to set up, but they’re incredibly powerful.
Tools You Can Use for SSH Through Firewall
Having the right tools makes all the difference. Here are some tools that can help you SSH through firewall:
1. OpenSSH
OpenSSH is the go-to tool for most users. It’s free, open-source, and highly customizable. You can use it to set up port forwarding, tunnels, and more.
2. PuTTY
PuTTY is a popular SSH client for Windows users. It’s easy to use and has a ton of features, including support for SSH tunneling.
3. Proxychains
Proxychains is a tool that forces any TCP connection through a chain of proxies. It’s perfect for bypassing firewalls that block direct connections.
With the right tools, SSH through firewall becomes a lot easier. You just need to know which ones to use and how to configure them.
Data and Statistics: The Numbers Behind SSH Through Firewall
Let’s look at some data to understand why SSH through firewall is so important. According to a report by Cisco, the number of firewalls deployed globally has increased by 30% in the past year alone. That means more networks are being protected, but it also means more restrictions for users who need secure access.
Another study by Statista shows that SSH is the most widely used protocol for secure remote connections. With more than 80% of IT professionals relying on SSH for their daily tasks, it’s clear that this protocol is here to stay.
These numbers highlight the growing need for solutions like SSH through firewall. As networks become more secure, users need to find ways to maintain their access without compromising on security.
Best Practices for SSH Through Firewall
Now that you know the strategies and tools, let’s talk about best practices. Here are some tips to keep in mind:
- Use Strong Authentication: Always use strong passwords or SSH keys for authentication.
- Limit Access: Restrict SSH access to only the necessary users and IPs.
- Monitor Connections: Keep an eye on your SSH connections to detect any suspicious activity.
Following these best practices ensures that your SSH through firewall setup is both effective and secure.
Common Mistakes to Avoid
Even the best of us make mistakes. Here are some common pitfalls to avoid when setting up SSH through firewall:
- Using Default Ports: Firewalls love to block port 22, so change it up.
- Ignoring Security: Don’t sacrifice security for convenience.
- Not Testing: Always test your setup to make sure it works as expected.
By avoiding these mistakes, you can ensure a smoother and more secure SSH experience.
Conclusion: Taking Your SSH Skills to the Next Level
And there you have it, folks. SSH through firewall might seem daunting at first, but with the right knowledge and tools, it’s totally doable. Whether you’re using port forwarding, SSH tunneling, or proxies, there’s a solution out there for everyone.
So, what’s next? Take what you’ve learned and start experimenting. Try setting up your own SSH through firewall connection and see how it works. And don’t forget to share your experiences in the comments below. Your feedback helps us all grow and learn.
Stay curious, stay secure, and keep exploring the world of SSH. Until next time, happy networking!
Table of Contents
- Understanding SSH: The Basics You Need to Know
- Why Firewalls Are Both a Blessing and a Curse
- SSH Through Firewall: The Challenges
- Strategies for SSH Through Firewall
- Tools You Can Use for SSH Through Firewall
- Data and Statistics: The Numbers Behind SSH Through Firewall
- Best Practices for SSH Through Firewall
- Common Mistakes to Avoid
- Conclusion: Taking Your SSH Skills to the Next Level

Detail Author:
- Name : Mr. Hiram Yost PhD
- Username : torp.lauriane
- Email : kaelyn76@yahoo.com
- Birthdate : 1987-08-31
- Address : 3534 Thurman Divide Apt. 539 West Lonzoview, IA 71023
- Phone : +1-914-520-8468
- Company : Kautzer Ltd
- Job : Warehouse
- Bio : Suscipit ut nesciunt alias deleniti. Omnis et eligendi necessitatibus et enim dolorem ullam.
Socials
twitter:
- url : https://twitter.com/telly9327
- username : telly9327
- bio : Id est similique et nihil. Sunt a quas voluptatum magnam rem. Ea deleniti consectetur vel. Ut sit voluptas aspernatur voluptates sunt sed assumenda.
- followers : 2248
- following : 2182
facebook:
- url : https://facebook.com/tellybradtke
- username : tellybradtke
- bio : Iusto et consequatur eos et tempore.
- followers : 479
- following : 316